Partners working within the Department of Energy’s Clean Energy Cybersecurity Accelerator (CECA) tested out a tool for closing the gaps within control systems used by commercial and industrial operations such as utilities, finding that active scanning for cyber vulnerabilities can be done without sacrificing any system functionality overall.
As part of the testing, CECA ran a test of the system using a photovoltaic solar power plant along with its substation and control center, integrating these to run with runZero, a cyber asset attack surface management product by a company of the same name. The PV plant was designed to emulate a small utility-owned solar generation plant, and it included SEL power system devices, a BESS, and a commercial-grade inverter, according to the DOE.
They also tested the solution at scale, integrating it with an environment that networked nearly 4000 AMI devices onto one flat network. This is large enough of an environment that it could represent the number of customers served by a large substation.
Utility partners Duke Energy and Berkshire Hathaway Energy co-sponsored the technical assessment of runZero, and the National Renewable Energy Laboratory (NREL) managed the project.
Read More: Why Defense-in-Depth Is Crucial for Utility Cyber Protection
CECA is an arm of the DOE’s Office of Cybersecurity, Energy Security, and Emergency Response. It is specifically tasked with developing solutions to protect the power grid from critical security concerns by working alongside utility industry collaborators.
CECA’s task is to test different tools on their ability to help close cybersecurity gaps that could represent a serious threat to critical infrastructure and help speed effective tools to the market by confirming their usefulness to the wider electric utility industry.
CECA’s Cohort 2 was specifically asked to examine the persistent challenge of operational technology (OT) asset management. The assessment was conducted in the NREL ARIES Cyber Range, which uses a collection of open-source and custom tools to emulate complex ICS systems, according to CESER.
The control systems used by commercial and industrial institutions are often a hodgepodge of different systems and techniques that grow organically over time, using products and tools from many different vendors over time. These may get the job done on a day-to-day basis, but they do not always operate with ideal security countermeasures in place. Gaps do often exist, and they can be hard to find, appraise and fix.
Cohort 2 from CECA looked at “hidden risks due to incomplete system visibility and device security and configuration,” according to the executive summary of CECA’s July report on its findings. The researchers also wanted solutions that didn’t rely too much on passive discovery of risks.
The cohort tested out a configurable tool for industrial control systems called runZero, which uses deployed agents to find information about individual assets and a server-fed user interface to gather and show information about every device used in a particular control system environment. The researchers found runZero was one tool within its class capable of performing these tasks without slowing down regular system operation.
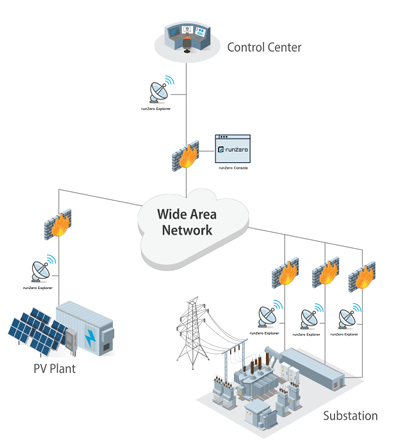
Users within a control system, such as those run by electric utilities, could gain a better analysis of vulnerabilities on the system with runZero to help make them more visible, according to the CESER report.
During the testing, researchers found that runZero could display detailed information about all devices used except for those not IP-addressable, meaning they needed to be networked through a remote terminal unit. The system’s active scanning methods had no impact on system performance, SCADA processes or communications.
This could mean that an active scanning product could be useful in more utility applications, although the reasearchers note that these testing results are not one size fits all and every industrial control system is a bit different from the next.
Read More: How to Address Security Concerns at the Network Level
CECA’s Cohort 2 plans to release the results of more testing later on in 2024.
“With evolving cybersecurity threats to U.S. energy systems, and with architectures changing as the grid modernizes, it is critical to drive adoption of innovative solutions,” Dan LaGraffe, Deputy Director of CESER’s Risk Management Tools and Technologies Division said in a DOE press release in July. “We’re optimistic that the testing and results from the CECA program will help advance tools, like runZero, that can help improve security and resilience across the sector.”
“We are seeing more and more sophisticated attacks against critical infrastructure, particularly energy infrastructure,” Rob King, Director of Research at runZero said in a release. “Working with CECA allowed us to prove that active scanning of operational technology (OT)/ICS infrastructure can be done safely and effectively and is important to securing these vital systems.”




